- Mit Cisco Anyconnect Free
- Mit Cisco Anyconnect Windows 10
- Cisco AnyConnect VPN - Massachusetts Institute Of Technology
- Off Campus? Connect Securely Through The MIT Remote Access ..
- Clear Cisco Vpn Cache
Installing Cisco VPN and using Remote Desktop. Installing Cisco VPN and using Remote Desktop. Azure rds login. Cisco's AnyConnect VPN is a Virtual Private Network (VPN) client. For more information about VPNs, see: Virtual Private Network at MIT. Installing Cisco VPN and using Remote Desktop. Installing Cisco VPN and using Remote Desktop. The Cisco AnyConnect Secure Mobility Virtual Private Network (VPN) Client provides privacy and security for your computing activities as well as the ability to access protected MIT resources that require a MITnet IP address such as fileshares, Forrester, and Remote Desktop.
Current Description
A vulnerability in the interprocess communication (IPC) channel of Cisco AnyConnect Secure Mobility Client for Windows could allow an authenticated, local attacker to cause a denial of service (DoS) condition on an affected device. To exploit this vulnerability, the attacker would need to have valid credentials on the Windows system. The vulnerability is due to insufficient validation of user-supplied input. An attacker could exploit this vulnerability by sending a crafted IPC message to the AnyConnect process on an affected device. A successful exploit could allow the attacker to stop the AnyConnect process, causing a DoS condition on the device. To exploit this vulnerability, the attacker would need to have valid credentials on the Windows system.
Analysis Description
A vulnerability in the interprocess communication (IPC) channel of Cisco AnyConnect Secure Mobility Client for Windows could allow an authenticated, local attacker to cause a denial of service (DoS) condition on an affected device. To exploit this vulnerability, the attacker would need to have valid credentials on the Windows system. The vulnerability is due to insufficient validation of user-supplied input. An attacker could exploit this vulnerability by sending a crafted IPC message to the AnyConnect process on an affected device. A successful exploit could allow the attacker to stop the AnyConnect process, causing a DoS condition on the device. To exploit this vulnerability, the attacker would need to have valid credentials on the Windows system.
Severity
CVSS 3.x Severity and Metrics: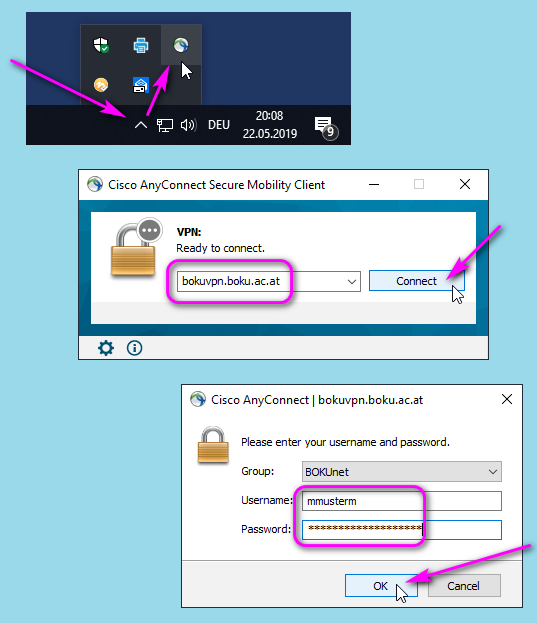
Weakness Enumeration
| CWE-ID | CWE Name | Source |
|---|---|---|
| CWE-20 | Improper Input Validation | NIST Cisco Systems, Inc. |
Known Affected Software Configurations Switch to CPE 2.2
Denotes Vulnerable Software
Are we missing a CPE here? Please let us know.
Change History
2 change records found show changesDepending on how your company configured Duo authentication, you may or may not see a “Passcode” field when using the Cisco AnyConnect client.
Single Password with Automatic Push
Mit Cisco Anyconnect Free
If AnyConnect only prompts for a password, like so:
After you submit your login information, an authentication request is automatically sent to you via push to the Duo Mobile app or as a phone call.
Alternatively, you can add a comma (“,”) to the end of your password, followed by a Duo passcode or the name of a Duo factor. Here's how:

| Type.. | To.. |
|---|---|
| password,passcode | Log in using a passcode, either generated with Duo Mobile, sent via SMS, generated by your hardware token, or provided by an administrator. Examples: 'mypass123,123456' or 'mypass123,1456789' |
| password,push | Push a login request to your phone (if you have Duo Mobile installed and activated on your iOS, Android, or Windows Phone device). Just review the request and tap 'Approve' to log in. |
| password,phone | Authenticate via phone callback. |
| password,sms | Get a new batch of SMS passcodes. Your login attempt will fail — log in again with one of your new passcodes. |
You can also add a number to the end of these factor names if you have more than one device registered. For example, push2 will send a login request to your second phone, phone3 will call your third phone, etc.
Examples
To use Duo Push if your password is 'hunter2', type:
To use the passcode '123456' if your password is 'hunter2', type:
Mit Cisco Anyconnect Windows 10
To send new SMS passcodes to your second phone if your password is 'hunter2', type:
The comma is Duo's default separator character between your password and the Duo factor. Your administrator may have changed this to a different character. Be sure to follow the instructions sent to you by your organization if they differ from what's shown here.
Second Password for Factor Selection
If AnyConnect shows a 'Second Password' input field (note that your AnyConnect administrator may have changed the 'Second Password' label to something else):
Use the 'Second Password' field to tell Duo how you want to authenticate. Here's how:
| Type.. | To.. |
|---|---|
| A passcode | Log in using a passcode, either generated with Duo Mobile, sent via SMS, generated by your hardware token, or provided by an administrator. Examples: '123456' or '1456789' |
| push | Push a login request to your phone (if you have Duo Mobile installed and activated on your iOS, Android, or Windows Phone device). Just review the request and tap 'Approve' to log in. |
| phone | Authenticate via phone callback. |
| sms | Get a new batch of SMS passcodes. Your login attempt will fail — log in again with one of your new passcodes. |
Cisco AnyConnect VPN - Massachusetts Institute Of Technology
You can also add a number to the end of these factor names if you have more than one device registered. For example, push2 will send a login request to your second phone, phone3 will call your third phone, etc.
Examples
To send a Duo Push request to your primary phone, type:
To send a Duo Push request to your secondary phone, type:
To use the passcode '123456', type:
Off Campus? Connect Securely Through The MIT Remote Access ..
Clear Cisco Vpn Cache
To send new SMS passcodes to your second phone, type:
